
CentOS 7 64bits
Squid Cache: Version 3.4.6
1 – Instalar CLAMAV
# install from EPEL [root@dlp ~]# yum --enablerepo=epel -y install clamav clamav-update [root@dlp ~]# sed -i -e "s/^Example/#Example/" /etc/freshclam.conf # update pattern files [root@dlp ~]# freshclam ClamAV update process started at Fri Aug 29 22:03:30 2014 main.cld is up to date (version: 55, sigs: 2424225, f-level: 60, builder: neo) daily.cvd is up to date (version: 19314, sigs: 1094505, f-level: 63, builder: neo) bytecode.cvd is up to date (version: 242, sigs: 46, f-level: 63, builder: dgoddard)
2 – Testar scaneamento
[root@dlp ~]# clamscan --infected --remove --recursive /home ----------- SCAN SUMMARY ----------- Known viruses: 3575245 Engine version: 0.98.4 Scanned directories: 2 Scanned files: 3 Infected files: 0 Data scanned: 0.00 MB Data read: 0.00 MB (ratio 0.00:1) Time: 10.369 sec (0 m 10 s) # faça download de um virus Trial: [root@dlp ~]# curl -O http://www.eicar.org/download/eicar.com # teste a remoção dele e veja saída do comando: [root@dlp ~]# clamscan --infected --remove --recursive . ./eicar.com: Eicar-Test-Signature FOUND ./eicar.com: Removed. # just detected ----------- SCAN SUMMARY ----------- Known viruses: 3575245 Engine version: 0.98.4 Scanned directories: 3 Scanned files: 10 Infected files: 1 Data scanned: 0.00 MB Data read: 256.57 MB (ratio 0.00:1)
3 – Instalação Clamav server
# install from EPEL [root@prox ~]# yum --enablerepo=epel -y install clamav-server clamav-server-systemd [root@prox ~]# cp /usr/share/doc/clamav-server*/clamd.conf /etc/clamd.d/squid.conf [root@prox ~]# vi /etc/clamd.d/squid.conf # Alterar esse arquivo de acordo: # line 8: Comente #Example # line 14: descomente e troque LogFile /var/log/clamd.squid # line 66: descomente e troque PidFile /var/run/clamd.squid/clamd.pid # line 70: descomente TemporaryDirectory /var/tmp # line 85: descomente e troque LocalSocket /var/run/clamd.squid/clamd.sock # line 101: descomente TCPSocket 3310 # 195: troque User squidclamav Adicionar o usuário (sem necessidade de login) [root@prox ~]# useradd -d /var/tmp -s /sbin/nologin squidclamav useradd: warning: the home directory already exists. Not copying any file from skel directory into it. # Criando o diretório [root@prox ~]# mkdir /var/run/clamd.squid Permissões do usuário ao diretório: [root@prox ~]# chown squidclamav. /var/run/clamd.squid [root@prox ~]# cp /usr/share/doc/clamav-server*/clamd.sysconfig /etc/sysconfig/clamd.squid [root@prox ~]# vi /etc/sysconfig/clamd.squid # 1, 2: descomente e troque CLAMD_CONFIGFILE=/etc/clamd.d/squid.conf CLAMD_SOCKET=/var/run/clamd.squid/clamd.sock [root@prox ~]# vi /etc/tmpfiles.d/clamd.squid.conf # crie um novo arquivo contendo: d /var/run/clamd.squid 0755 squidclamav squidclamav - [root@prox ~]# vi /usr/lib/systemd/system/clamd@.service # Adicionar as seguintes linhas ao final do arquivo: [Install] WantedBy=multi-user.target [root@prox ~]# touch /var/log/clamd.squid [root@prox ~]# chown squidclamav. /var/log/clamd.squid [root@prox ~]# chmod 600 /var/log/clamd.squid # Adicionando para inicialização automática junto ao boot: [root@prox ~]# systemctl start clamd@squid [root@prox ~]# systemctl enable clamd@squid ln -s '/usr/lib/systemd/system/clamd@.service' '/etc/systemd/system/multi-user.target.wants/clamd@squid.service'
4 – Instalação do icap
[root@prox ~]# yum -y install gcc make
[root@prox ~]# curl -O http://ftp.jaist.ac.jp/pub/sourceforge/c/project/c-/c-icap/c-icap/0.3.x/c_icap-0.3.4.tar.gz
[root@prox ~]# tar zxvf c_icap-0.3.4.tar.gz
[root@prox ~]# cd c_icap-0.3.4
[root@prox c_icap-0.3.4]# ./configure
[root@prox c_icap-0.3.4]# make
[root@prox c_icap-0.3.4]# make install
[root@prox c_icap-0.3.4]# cd
[root@prox ~]# cp /usr/local/etc/c-icap.conf /etc
[root@prox ~]# vi /etc/c-icap.conf
# line 140: troque para seu email
ServerAdmin root@server.world
# line 149: coloque o hostname do servidor em questão
ServerName prox.server.world
# line 500: add
Service squidclamav squidclamav.so
[root@prox ~]# vi /etc/tmpfiles.d/c-icap.conf
# crie um novo arquivo contendo
d /var/run/c-icap 0755 root root -
# Criar o arquivo de inicialização com o conteúdo abaixo.
[root@prox ~]# vi /etc/rc.d/init.d/c-icap
# ----------------- COMEÇA AQUI ----------------------------
#!/bin/bash
# c-icap: Start/Stop c-icap
# chkconfig: - 70 30
# description: c-icap is an implementation of an ICAP server.
# processname: c-icap
# pidfile: /var/run/c-icap/c-icap.pid
. /etc/rc.d/init.d/functions
. /etc/sysconfig/network
CONFIG_FILE=/etc/c-icap.conf
PID_DIR=/var/run/c-icap
RETVAL=0
start() {
echo -n $"Starting c-icap: "
daemon /usr/local/bin/c-icap -f $CONFIG_FILE
RETVAL=$?
echo
[ $RETVAL -eq 0 ] && touch /var/lock/subsys/c-icap
return $RETVAL
}
stop() {
echo -n $"Stopping c-icap: "
killproc c-icap
rm -f /var/run/c-icap/c-icap.ctl
RETVAL=$?
echo
[ $RETVAL -eq 0 ] && rm -f $PID_DIR/c-icap.pid /var/lock/subsys/c-icap
return $RETVAL
}
case "$1" in
start)
start
;;
stop)
stop
;;
status)
status c-icap
;;
restart)
stop
start
;;
*)
echo $"Usage: $0 {start|stop|status|restart}"
exit 1
esac
exit $?
# ----------------- TERMINA AQUI ----------------------------
# Atribua as permissões
[root@prox ~]# chmod 755 /etc/rc.d/init.d/c-icap
5 – Instalação squid clamav
[root@prox ~]# curl -L -O http://downloads.sourceforge.net/project/squidclamav/squidclamav/6.11/squidclamav-6.11.tar.gz [root@prox ~]# tar zxvf squidclamav-6.11.tar.gz [root@prox ~]# cd squidclamav-6.11 [root@prox squidclamav-6.11]# ./configure --with-c-icap [root@prox squidclamav-6.11]# make [root@prox squidclamav-6.11]# make install [root@prox squidclamav-6.11]# cd [root@prox ~]# ln -s /usr/local/etc/squidclamav.conf /etc/squidclamav.conf #Procure pelo arquivo clwarn.cgi.pt_BR e copie ele para o diretório do apache cgi-bin [root@prox ~]# cp /usr/src/squidclamav-6.11/cgi-bin/clwarn.cgi.pt_BR /var/www/cgi-bin/ [root@prox ~]# vi /etc/squidclamav.conf # line 17: Troque para o local onde copio o arquivo clwarn.cgi.pt_BR redirect http://192.168.254.254:81/cgi-bin/clwarn.cgi.pt_BR # line 26: troque para igual o sock do clamd clamd_local /var/run/clamd.squid/clamd.sock # Adicionando na inicialização junto ao boot [root@prox ~]# systemctl start c-icap [root@prox ~]# chkconfig --add c-icap [root@prox ~]# chkconfig c-icap on
6 – Adicionando os parâmetros ao final do squid
[root@prox ~]# vi /etc/squid/squid.conf icap_enable on icap_send_client_ip on icap_send_client_username on icap_client_username_header X-Authenticated-User icap_preview_enable on icap_preview_size 1024 icap_service service_req reqmod_precache bypass=1 icap://127.0.0.1:1344/squidclamav adaptation_access service_req allow all icap_service service_resp respmod_precache bypass=1 icap://127.0.0.1:1344/squidclamav adaptation_access service_resp allow all
7 – Restart do squid e teste
systemctl restart squid
Instalar:
yum install perl-CGI
Conferir parametros cgi no apache.
Obs: Seria interessante realizar um restart do servidor para averiguar se todos os serviços subirão automaticamente.
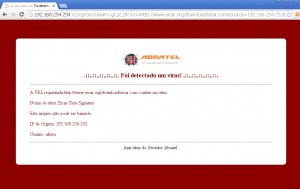
Entre no site http://eicar.org/85-0-Download.html e clique sobre o “eicar.com” que eh um virus trial para teste.
Deverá apresentar a tela do Clamav bloqueando o acesso como abaixo:
8 – Adicionar no crontab a atualização do antivirus e procura dos virus
# Atualizando a base de dados do clamav diariamente:
00 1 * * * /usr/bin/freshclam > /dev/null &> /dev/null
# Varrendo diretorios com clamav e enviando os virus para o diretorio INFECTADOS criado
00 23 * * * /usr/bin/clamscan -r –move=/storage1/infectados /share/publica
00 20 * * * /usr/bin/clamscan -r –move=/storage1/infectados /var/www